
Whatever heights the technology may reach for protecting privacy, there is always a sneaky peaky mouse willing to steal the cheese. Ethical Hacking is the legalisation of stealing cheese while adhering to certain norms. The foremost basics of hacking include getting certifications that are approved by the Ethical Hacking Course in Chennai. Ethical hackings are just malicious hackings that are considered legal for any purpose like national security or to protect a company’s confidential data. Before learning the skills for hacking, know the key principles of Ethical Hacking and how it is differentiated from malicious hacking.
What is Ethical Hacking?
Hacking is finding potential entry points into a computer system or computer network and then successfully penetrating them. Hacking is typically carried out to obtain unauthorised access to a computer network or system to damage the network or steal sensitive data stored on the computer. As long as it is done to uncover flaws in a computer or network system for testing purposes, hacking is typically legal. This type of hacking is commonly known as ethical hacking.
Key Principles of Ethical Hacking
Ethical hackers follow four major protocols that a typical malicious hacker fails to do. Individuals desiring to become ethical hackers should abide by these principles besides fulfilling the ethical hacking prerequisites.
- Adhering to the law - Ensure you have the necessary permissions before accessing and doing a security evaluation.
- Determining the tasks - Make that the ethical hacker's work is legal and within the organization's permitted parameters by determining the scope of the evaluation.
- Reporting and Resolving - Every vulnerability found during the assessment should be communicated to the company. Providing suggestions for resolving these security issues.
- Sensitive Standard of Data - Depending on the sensitivity of the information, ethical hackers may need to sign a non-disclosure agreement in addition to any conditions and limitations set by the inspected firm.
Who is a Certified Ethical Hacker?
Ethical hackers evaluate the servers, networks, and computer security or technologies used by the business. The main responsibility is to locate the attackers, track them down, and report them to the vigilance division. Alternately, they try using white ethical hacking techniques or approaches to fix the problems caused by the assault. The goal of ethical hacking is different from criminal hacking in that it requires prior IT organisation clearance. The basics of hacking involve a few responsibilities as follows,
- They conduct meetings with clients to review the installed security system.
- Investigating the firm's system, network architecture, and potential entry points.
- They perform several system penetration tests.
- Locating and documenting security weaknesses and violations.
- They locate areas with high security.
- Evaluation and assessment of the security network.
- They generate ideas for security enhancements.
- Assembling reports from penetration tests for the client.
- They conduct penetration tests after introducing new security measures.
- They provide alternate upgrade suggestions.
Enrol in the Ethical Hacking Course in Bangalore to learn how to carry out these duties effectively and secure a system or network from malicious hackers stealing the company’s confidentiality.
Ethical Hackers Vs Malicious Hackers
The term "ethical hackers" refers to someone who uses their hacking abilities for legal purposes, frequently collaborating with businesses and organisations to advance their cybersecurity. Conversely, “malicious hackers” employ their abilities for illegal or disruptive activities.
Motivation is a significant distinction between malicious and ethical hackers. The goal of ethical hackers is to increase security and make the world a safer place. On the other side, malicious hackers are driven by monetary gain or a desire to harm. Another important distinction is that while criminal hackers frequently lack authorization, ethical hackers frequently have it. The ethical hacker and the company they work with will frequently sign a contract or agreement as proof of this consent.
The skills for hacking are similar in both cases, yet they differ in motivations and authorisation levels, distinguishing them as two very different types of persons. While malicious hackers constitute a major threat to both individual users and organisations, ethical hackers play an important role of maintaining the security of our systems and data.
10 Important Skills of an Ethical Hacker

Computer Networking Skills
The ability to network effectively is one among the most crucial abilities for ethical hackers. This makes it inevitable for you to join the CCNA Course in Chennai at FITA Academy and learn about different types of networks and their functions. The connectivity of several devices is commonly referred to as hosts. They are connected using a variety of pathways to send and receive data or media, which is all that build a computer network. Ethical hacking helps to study the numerous interconnected machines in a network and their potential security concerns. They also find ways to mitigate those threats by understanding the basics of hacking through networks like DHCP, Suoernetting, Subnetting, and more.
Programming Skills
Programming knowledge allows you to give computer system commands to carry out tasks known as "code". Computer programmers create these programmes to carry out a certain activity. Technical and logical components merge in computer programming abilities. Numerous hacker programming language are used to write code, including C, C++, Java, Python, C#, .Net, JavaScript, HTML, and PHP. These programming languages are essential for an ethical hacker since they may have flaws or errors. Join the Java Training in Bangalore to lay the foundation in the basics of hacking.
Hardware Knowledge
A rudimentary understanding of computer hardware is necessary for an ethical hacker. The physical components of a computer, such as the CPU, monitor, mouse, keyboard, computer data storage, graphics card, sound card, speakers, and motherboard, are referred to as computer hardware.
Conversely, the set of instructions that can be stored and executed by hardware is referred to as software. So, in order to hack a machine run by a computer, one must be familiar with the machine or understand its operation. The next stage is to log into the computer running the device. Therefore, it is the basics of hacking to have a fundamental understanding of hardware.
Linux Skills
The Linux operating system family is a collection of free and open-source Unix-like platforms based on the Linux Kernel. It is an open-source operating system. The GNU General Public License allows for the modification and distribution of the source code to anyone for commercial or non-commercial use.
An ethical hacker should focus on learning Linux because it is the most secure operating system in terms of security. Take this Linux Online Course to learn more about its role in the hacking. Although there is malware for Linux, it is less vulnerable than any other operating system. This does not infer that Linux is completely secure. Yet, no anti-virus software is needed.
Knowledge of Web Applications
The foundation of online businesses is web applications. Web applications are used by everyone connected to the internet for a variety of functions, such as social networking, online shopping, email, and chat. Web applications are increasingly exposed to more complex attack methods.
Ethical hackers can comprehend web attacks and know the web application hacking techniques employed by cybercriminals with an understanding of web development. It is one of the most in-demand ethical hacking prerequisites of the sector. An ethical hacker can use these approaches to evaluate the protection provided by their company against web application assaults.
Cryptographic Skills
The study and use of methods for secure communication in the presence of outside parties as adversaries are known as cryptography. It involves creating and assessing protocols that stop nefarious third parties from obtaining information communicated between two entities and so upholding the many facets of information security. An ordinary text or communication, known as plain text, is changed during transmission into an unintelligible form, known as ciphertext, which renders it unreadable to hackers. Making sure that information does not leak within the organisation is the responsibility of an ethical hacker. Consider enrolling in the Cyber Security Course in Chennai to learn more about securing networks and systems from hackers.
Knowledge of Reverse Engineering
Reverse Engineering is the process of estimating a product's functions, design, and requirement specifications by examining its source code. It creates a programme database and uses this to produce information. Reverse engineering aims to create documentation for a legacy system and speed up maintenance work by making a system easier to understand. Reverse engineering is frequently used in software security to ensure the system is free of any significant security flaws or vulnerabilities. It contributes to a system's robustness, defending it against spyware and hackers. Some developers even go as far as ethically hacking their own systems to find flaws.
Database Management System (DBDS) Skills
The foundation for building and maintaining databases is DBMS. Accessing a database where all the information is kept can pose a serious threat to the business. Thus it's crucial to make sure this software is hacker-proof. It is one of th basic skills for hacking used widely. To assist the company in creating a robust DBMS, an ethical hacker must have a solid understanding of this and various database engines and data structures.
Wireless Technologies
Ethical hackers can prevent computers from delivering information via inaudible waves by learning wireless technologies like WEP, WPA, WPA2, WPS, etc. A thorough understanding of wireless technology may set up a protocol for connection, authentication, and limitations. You can join the CCNA Course in Bangalore as it throws light on all the wired and wireless network connections of systems and the Internet Of Things.
Critical Thinking and Problem Solving Skills
Problem Solving Skills help find a problem's root cause and make an effective solution possible. In addition to the technical abilities mentioned above, an ethical hacker needs to be able to think critically and solve problems quickly. They must be eager to pick up new techniques and ensure that all security gaps are carefully examined. It takes a lot of testing and a creative desire to develop new approaches to solve problems.
Purpose of Programming Languages in Ethical Hacking
| S.No. | Programming Language | Description | Platform | Purpose |
|---|---|---|---|---|
|
1. |
HTML |
Used for writing web pages |
Cross-platform |
Web Hacking HTML forms are used to collect data through login forms and other online data entry processes. You can easily find and take advantage of flaws in the code if you can create and read HTML. |
|
2. |
JavaScript |
Scripting language used on the client side |
Cross-platform |
Web Hacking The client browser runs JavaScript code. It can be used for cross-site scripting, reading saved cookies, and other purposes. |
|
3. |
PHP |
Scripting language used on the server side |
Cross-platform |
Web Hacking PHP processes HTML forms and completes other unique duties. It can be used to build custom applications that alter web server settings and leave them open to intrusion. |
|
4. |
Used to communicate with database |
Cross-platform |
Web Hacking Bypassing lousy web application login algorithms with SQL injection, deleting data from the database, etc. |
|
|
5. |
Python Ruby Bash Perl |
High-level programming languages |
Cross-platform |
Building Scripts and Tools When you need to create automation tools and scripts, they are useful. The acquired information can also be used to comprehend and customise existing tools. |
|
6. |
CSharp Visual Basic VBScript |
Other programming languages |
Java and CSharp are cross-platform. Visual Basic is for windows. |
The usage depends on the scenario |
|
7. |
C & C++ |
Low-level programming languages |
Cross-platform |
Writing Shell Codes, Exploits, etc. They are quite helpful when you need to create your own shell codes, exploits, and rootkits or when you need to comprehend and improve upon existing ones. |
Since Python is considered an all-purpose programming language it is a widely used hacker programming language. Join the Python Training in Chennai to master the language.
Growing Demand for Ethical Hacking
The demand for ethical hackers rises as technology is used more in daily life. Before malicious hackers can take advantage of vulnerabilities, ethical hackers must test systems and find them. Ethical hackers have a wide range of professional options. While some operate as independent consultants, others hold jobs with businesses or governmental agencies. Many ethical hackers also focus on a certain field, such as network security or online security. In the looming years, it is anticipated that demand for ethical hacking services would increase even more. This is because corporations need to defend their systems from assault and cyber threats keep evolving.
Apart from learning the basics of hacking, you can also learn the exclusive ways for protection by taking up the Cyber Security Online Course. It has similar demands and falls under the same domain.
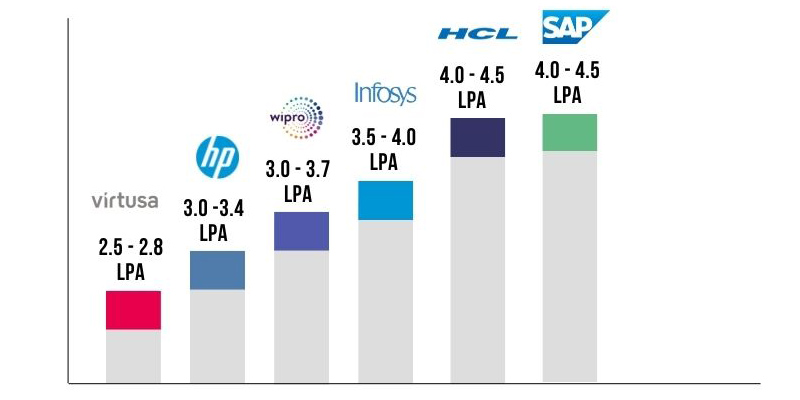
Ethical Hacking Salary for Freshers
Ethical Hackers are paid well since protecting a company’s confidential data is crucial. The average fresher salary for an ethical hacker falls between INR 3.0 to 4.5 LPA. This gets varied with different companies, their location, candidates' experience and technical skills.
Ethical Hacking could be the best example that goes with the proverb, ‘Diamond cuts diamond’. To prevent our data and privacy from being stolen and protect our systems from hackers, we need saviours who are ethical hackers. Take up this Ethical Hacking Online Course and fetch a high-paying designation in a top popular company. Because, no matter the size of the trap, there is always a cheese-stealing mouse.
Recent Post: Software Tester Salary for Freshers
