
The landscape of ethical hacking, also known as penetration testing, has undergone significant transformation with the introduction of automated tools. Various tools designed to expedite the testing process are currently in development.Enhancing one's work requires ethical hacking the security posture of organizations by assisting them in better protecting their information and systems. It serves as an effective means to enhance the expertise of security professionals within an organization. Integrating ethical hacking into an organization's security initiatives can prove to be highly beneficial. For those looking to delve into the world of ethical hacking and stay abreast of the latest tools and techniques, considering enrolling in a reputable Ethical Hacking Course in Chennai can provide valuable insights and skills. This learning opportunity provides people with the information they need to contribute effectively to the cybersecurity landscape and protect organizations from evolving threats.
What Are Hacking Tools and Software?
Hacking is the process of utilizing various tools or technologies, often in the form of computer programs and scripts, to gain access to unauthorized data as part of assessing the security measures of a computer system or network.
Hacking tools and software are essentially computer programs or intricate scripts developed by programmers. These tools are employed by hackers to identify vulnerabilities in computer operating systems, various web applications, servers, and networks. In contemporary settings, many employers, particularly in sectors like banking, utilize ethical hacking tools to enhance the security of their data against potential attackers. These hacking tools are available in either open-source form (freeware or shareware) or as commercial solutions. Individuals can also download such tools from the internet, particularly if they intend to use them for malicious purposes.
Ethical hacking tools are employed by security professionals, particularly to access computer systems and identify vulnerabilities, contributing to the enhancement of their security. These professionals utilize various hacking tools such as packet sniffers for intercepting network traffic, password crackers to uncover passwords, and port scanners to identify open ports on computers. It is crucial to emphasise the ethical and responsible use of these tools, ensuring their intended purpose aligns with security improvement.
The field of network administration has experienced significant growth, evolving from simple network monitoring to the management of diverse elements such as firewalls, intrusion detection systems (IDS), VPNs, anti-virus software, and anti-spam filters.
Several notable hacking tools are prevalent in the market, including Nmap (Network Mapper), Nessus, Nikto, Kismet, NetStumbler, Acunetix, Netsparker, Intruder, Metasploit, Aircrack-Ng, among others. These tools serve various purposes within ethical hacking practices, contributing to the assessment and reinforcement of cybersecurity measures.
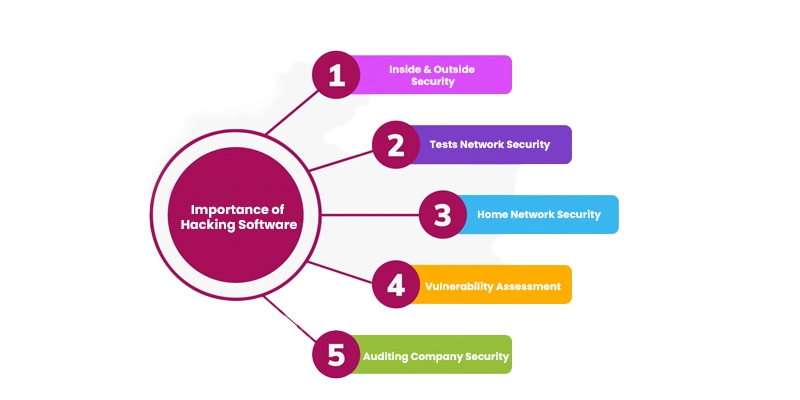
Importance of Hacking Software
When it comes to hacking software, there is often a sense of anxiety or paranoia about the potential damage it may cause to computer systems. However, the reality is quite different, as employers may require professional experts in ethical hacking to safeguard critical data, valuable assets, and hardware and software systems from potential attackers. The importance of ethical hacking has become evident, leading to the hiring of ethical hackers by companies. Here are some key features of hacking software:
Provides Inside and Outside Security
Hacking software offers both internal and external security against threats for end-users.
Tests Network Security
Ethical hacking software is utilized to test the security of networks by identifying vulnerabilities and addressing them.
Downloadable for Home Network Security
Individuals can download ethical hacking software for their home network security from open-source platforms, allowing them to secure it from potential threats.
Vulnerability Assessment
Ethical hacking software is employed for vulnerability assessments, enabling the protection of networks or systems from external attacks.
Auditing Company Security
It is used to audit the security of a company, ensuring that the computer systems are running smoothly with no issues.
These features highlight the constructive and protective role that ethical hacking software plays in enhancing security measures, both for individual users and organizations.
The Best Ethical Hacking Resources to Keep an Eye on in 2024

1. Invicti
Invicti is a web application security scanner, a hack application and hacking tool designed to automatically identify SQL Injection, XSS, and vulnerabilities in web applications or services. Typically available as a Software as a Service (SAAS) solution, Invicti comes with the following features:
-
Dead Accurate Vulnerability Detection
Invicti employs unique Proof-Based Scanning Technology to provide precise and accurate vulnerability detection.
-
Minimal Configuration and Scalable Solution
The tool requires minimal configuration, offering a scalable solution to adapt to varying security needs.
-
Automatic Detection of URL Rewrite Rules and Custom 404 Error Pages
Invicti automatically identifies URL rewrite rules and custom 404 error pages, enhancing its adaptability to diverse web environments.
-
REST API for Seamless Integration
It provides a REST API that allows seamless integration with Software Development Life Cycle (SDLC) processes and bug tracking systems.
-
High Scanning Capacity
Invicti boasts the capability to scan over 1,000 web applications within a 24-hour timeframe, demonstrating its efficiency in handling large-scale security assessments.
-
Pricing
The pricing for Invicti Security features ranges from $4,500 to $26,600.
Invicti stands out as a comprehensive web application security tool, offering advanced scanning technology and integration capabilities to enhance the security posture of web applications and services. For those looking to deepen their understanding of web application security tools and explore how to effectively integrate them into security protocols, considering enrolling in a reputable Ethical Hacking Course in Bangalore can provide valuable insights and skills. This learning opportunity provides people with the information they need to navigate and utilize advanced security tools like Invicti, contributing to the robust cybersecurity measures needed to safeguard web applications against potential threats.
2. Fortify WebInspect
Fortify WebInspect is an advanced hacking tool that specializes in comprehensive dynamic analysis security for complex web applications and services. Here are some key features of this tool:
-
Dynamic Behavior Analysis
Fortify WebInspect excels in identifying security vulnerabilities by conducting dynamic analysis, allowing it to test the dynamic behavior of running web applications.
-
Scanning Control
The tool provides control over the scanning process by gathering relevant information and statistics, ensuring a focused and efficient vulnerability assessment.
-
Centralized Program Management
Fortify WebInspect offers centralized program management capabilities, including vulnerability trending, compliance management, and risk oversight. This makes it a versatile tool suitable for both professional-level testing and novice security testers.
-
Simultaneous Crawl
The tool supports simultaneous crawling, enabling it to conduct professional-level testing efficiently.
-
Comprehensive Security Testing
Fortify WebInspect provides a high level of security testing, covering a range of vulnerabilities in web applications and services.
-
Pricing
The cost of Fortify WebInspect is approximately $29,494.00, as provided by HP company. This cost includes features related to Tran security and virus protection.
Fortify WebInspect, offered by HP, stands as a robust solution for organizations seeking advanced dynamic analysis security for their web applications, with features catering to both experienced security professionals and those new to security testing.
3. Cain & Abel
Cain & Abel is a versatile password recovery tool provided by Microsoft. Here are some of its key features:
-
MS Access Password Recovery
Cain & Abel is utilized for the recovery of MS Access passwords, providing a solution for users who need to regain access to their Microsoft Access databases.
-
Network Sniffing
The tool supports network sniffing capabilities, allowing users to analyze and capture network traffic for various purposes, including security assessments.
-
Password Uncovering
Cain & Abel has the ability to uncover password fields, providing visibility into obscured or hidden passwords.
-
Password Cracking Techniques
The tool employs various password cracking techniques, including dictionary attacks, brute-force attacks, and cryptanalysis attacks, to crack encrypted passwords.
-
Free and Open Source
Cain & Abel is freely available as an open-source tool. Users can download it without incurring any costs.
Cain & Abel serves as a multi-functional tool, offering password recovery capabilities, network sniffing, and password cracking features. As a free and open-source tool, it provides users with a cost-effective solution for various password-related and network analysis tasks.
4. Nmap (Network Mapper)
Nmap, also known as Network Mapper, is considered one of the finest hacking tools, particularly for port scanning, a crucial phase in ethical hacking. Originally a command-line tool developed for Linux or Unix-based operating systems, it now also has a version compatible with Windows.
Key Features of Nmap:
-
Network Security Mapper
Nmap serves as a network security mapper, proficient in discovering services and hosts on a network, allowing for the creation of detailed network maps.
-
Host and Service Discovery
The software excels in host discovery and service detection on a network, providing comprehensive insights into the network's structure and components.
-
Operating System Detection
Nmap includes features for detecting the operating systems running on hosts within the network, enhancing its utility in ethical hacking scenarios.
-
Script Extensibility
Nmap is script-extensible, allowing users to incorporate advanced vulnerability detection scripts, thus enhancing its capabilities for security assessments.
-
Adaptability to Network Conditions
The tool can adapt to varying network conditions, including congestion and latency, ensuring reliable scanning even in challenging environments.
Nmap's versatility and functionality make it a valuable tool for ethical hackers, penetration testers, and network administrators. With its ability to provide detailed insights into network structures and potential vulnerabilities, Nmap remains a widely used and respected tool in the field of cybersecurity.
5. Nessus
Nessus is a renowned ethical hacking tool, widely recognized as the world's most prominent vulnerability scanner. Developed by Tenable Network Security, Nessus is recommended for non-enterprise usage and is available for free. It specializes in efficiently identifying critical vulnerabilities on various systems.
Key Features of Nessus
-
Vulnerability Detection
Nessus is an effective network vulnerability scanner that can find many different kinds of system flaws.
-
Identification of Unpatched Services and Misconfigurations
The tool excels in identifying vulnerabilities related to unpatched services and misconfigurations, offering insights into potential security weaknesses.
-
Password Strength Assessment
Nessus is capable of assessing password strength, highlighting weak or default passwords that may pose a security risk.
-
System Vulnerability Detection
It is adept at detecting various system vulnerabilities, providing a comprehensive assessment of potential security threats.
Nessus is highly regarded for its effectiveness in identifying critical bugs and security vulnerabilities in systems. While its free version is suitable for non-enterprise usage, it remains a valuable asset for security professionals, ethical hackers, and organizations looking to enhance their cybersecurity posture. For individuals seeking to harness the power of tools like Nessus and deepen their expertise in identifying and mitigating security vulnerabilities, enrolling in a reputable Ethical Hacking Course in Coimbatore can provide valuable insights and skills. This learning opportunity provides people with the information they need to effectively utilize security tools and contribute to the robust cybersecurity measures needed in today's digital landscape.
6. Nikto
Nikto is a powerful web scanner designed to scan and test various web servers, identifying outdated software, potentially dangerous CGIs or files, and other security issues. It performs both server-specific and generic checks, capturing received cookies in the process. Nikto is an open-source tool available for free, offering extensive capabilities for security assessments.
Key Features of Nikto
-
Open-Source Tool
Nikto is an open-source tool, making it freely available for security professionals and ethical hackers.
-
Identification of Potentially Dangerous CGIs or Files
The tool checks web servers and identifies over 6400 potentially dangerous CGIs or files, providing insights into security vulnerabilities.
-
Version-Specific Problem Detection
Nikto checks servers for outdated versions and version-specific problems across a wide range of servers, ensuring a comprehensive security assessment.
-
Plugin and Misconfigured File Checks
It performs checks on plugins and identifies misconfigured files, contributing to a thorough evaluation of web server security.
-
Identification of Insecure Programs and Files
Nikto excels in identifying insecure programs and files, helping users pinpoint and address potential security risks.
Nikto stands out as a valuable tool for web server security assessments, offering a wide range of features to identify vulnerabilities and potential threats. Its open-source nature makes it accessible to a broad user base within the ethical hacking and cybersecurity communities.
7. Kismet
Kismet is a highly effective ethical hacking tool utilized for testing wireless networks, including the hacking of wireless LAN or wardriving. It operates by passively identifying networks, collecting packets, and detecting non-beaconing and hidden networks through data traffic analysis.
Key Features of Kismet
-
Passive Network Identification
Kismet passively identifies wireless networks, making it an efficient tool for assessing the security of wireless LANs.
-
Packet Collection
The tool collects packets from wireless networks, enabling detailed analysis of network traffic and potential vulnerabilities.
-
Detection of Non-Beaconing and Hidden Networks
Kismet has the capability to detect non-beaconing and hidden networks, providing insights into networks that may not be readily visible.
-
Sniffer and Wireless Network Detector
It operates as both a sniffer and a wireless network detector, making it a versatile tool for a range of wireless network security assessments.
-
Support for Raw Monitoring Mode
Kismet supports raw monitoring mode, allowing users to gather data directly from wireless cards and enhancing its capabilities for in-depth network monitoring. To know more about this please visit FITA Academy right now.
-
Platform Compatibility
Kismet primarily runs on Linux-based operating systems, including Ubuntu and BackTrack, and is occasionally applicable to Windows environments.
Kismet's focus on wireless network testing and detection, along with its ability to operate as a sniffer, makes it a valuable tool for ethical hackers and security professionals assessing the security of wireless networks. Its compatibility with Linux systems enhances its appeal in various ethical hacking scenarios.
8. NetStumbler
NetStumbler is a noteworthy ethical hacking tool employed for preventing wardriving. Designed for Windows-based operating systems, it specializes in detecting IEEE 802.11g, 802.11a, and 802.11b networks. A newer version known as MiniStumbler is also available, offering additional features.
Key Uses of NetStumbler
-
Identification of Access Point (AP) Network Configuration
NetStumbler is utilized for identifying the network configuration of Access Points (APs), providing insights into the characteristics of wireless networks.
-
Interference Detection
The tool is capable of finding sources of interference, helping users identify and mitigate factors that may impact wireless network performance.
-
Signal Strength Assessment
NetStumbler assesses the strength of signals received from wireless networks, contributing to the evaluation of signal quality and coverage.
-
Detection of Unauthorized Access Points
It is quite good at identifying unapproved access points, which helps identify possible security threats and unapproved network access.
NetStumbler's focus on preventing wardriving, coupled with its ability to assess network configuration, interference, signal strength, and unauthorized access points, positions it as a valuable tool in the arsenal of ethical hackers and network security professionals. Its compatibility with Windows environments enhances its usability in various ethical hacking scenarios.
9. Acunetix
Acunetix is a fully automated ethical hacking tool that excels in detecting and reporting on over 4500 web vulnerabilities, encompassing various types of XSS (Cross-Site Scripting) and SQL Injection. It offers robust support for JavaScript, HTML5, and single-page applications, making it suitable for auditing complex authenticated applications.
Key Features of Acunetix
-
Automated Vulnerability Detection
Acunetix automates the process of detecting and reporting on a wide range of web vulnerabilities, providing a comprehensive assessment of potential security risks.
-
Support for JavaScript, HTML5, and Single-Page Applications
The tool is equipped to handle the complexities of modern web applications, supporting JavaScript, HTML5, and single-page applications during the auditing process.
-
Consolidated View
Acunetix provides a consolidated view of scan results, offering a clear and organized presentation of identified vulnerabilities.
-
Integration with Other Platforms and Tools
It allows for the integration of scanner results into other platforms and tools, facilitating a seamless workflow for security professionals.
-
Risk Prioritization
Acunetix prioritizes identified risks based on data, aiding users in focusing on the most critical vulnerabilities and addressing them promptly.
Acunetix's focus on automation, extensive vulnerability coverage, and support for modern web technologies make it a valuable asset for ethical hackers and security professionals conducting web application assessments. Its ability to prioritize risks and integrate with other tools enhances its usability in diverse security scenarios.
10. Netsparker
Netsparker is a powerful ethical hacking tool designed to mimic the approach of hackers, identifying vulnerabilities in web APIs and web applications, including common issues like cross-site scripting (XSS) and SQL Injection.
Key Features of Netsparker
-
Online Service or Windows Software
Netsparker is available both as an online service and as Windows software, providing flexibility in how users prefer to access and utilize the tool.
-
Verification of Identified Vulnerabilities
One of its standout features is the unique verification of identified vulnerabilities, demonstrating their authenticity and reducing false positives. The results have an additional degree of trustworthiness thanks to this verification process.
-
Time-Saving Automation
By automating the verification process and doing away with the necessity for manual vulnerability confirmation, Netsparker is made to save time. This efficiency enhances the overall workflow for security professionals.
Netsparker's focus on mimicking hacker methodologies, coupled with its ability to verify vulnerabilities and automate processes, positions it as a valuable asset for ethical hackers and security experts. The tool's availability as both an online service and standalone software adds versatility to its usage in various ethical hacking scenarios. For those looking to enhance their skills in utilizing advanced security tools like Netsparker and understanding how to integrate them effectively into ethical hacking practices, considering enrolling in a reputable Ethical Hacking Course in Trichy can provide valuable insights and skills. This learning opportunity provides people with the information they need to leverage tools responsibly and contribute to the robust cybersecurity measures needed in the ever-evolving landscape of ethical hacking.
11. Intruder
Intruder is a fully automated ethical hacking tool designed to scan for cybersecurity weaknesses, articulate the identified risks, and assist in remediation efforts. It streamlines vulnerability management by offering over 9000 security checks and includes features that prioritize results, integrate with popular platforms, and proactively scan systems for the latest vulnerabilities.
Key Features of Intruder
-
Comprehensive Security Checks
Intruder conducts over 9000 security checks, identifying missing patches, misconfigurations, and common web application issues like cross-site scripting (XSS) and SQL Injection.
-
Integration with Slack, Jira, and Major Cloud Providers
The tool seamlessly integrates with collaboration platforms such as Slack and issue tracking systems like Jira. Additionally, it provides compatibility with major cloud providers, enhancing its adaptability to different environments.
-
Result Prioritization Based on Context
Intruder prioritizes scan results based on context, allowing users to focus on addressing the most critical vulnerabilities first. This feature aids in efficient risk management.
-
Proactive Vulnerability Scanning
The tool proactively scans systems for the latest vulnerabilities, ensuring that security assessments remain up-to-date and reflective of the evolving threat landscape.
Intruder's emphasis on automation, comprehensive security checks, and integrations with popular platforms make it a valuable asset for ethical hackers and security professionals seeking an efficient and proactive approach to vulnerability management. Its ability to prioritize results based on context enhances its usability in diverse security scenarios.
12. Nmap (Network Mapper)
Nmap is a versatile open-source security and port scanner, recognized as a network exploration tool. It caters to both single hosts and large networks, making it a go-to choice for cybersecurity experts. Nmap serves purposes such as network inventory, monitoring host and service uptime, and facilitating service upgrade schedules.
Key Features of Nmap
-
Platform Compatibility
Nmap offers binary packages for various operating systems, including Windows, Linux, and Mac OS X, ensuring accessibility across diverse environments.
-
Data Transfer, Redirection, and Debugging Tool
Beyond its scanning capabilities, Nmap includes functionality as a data transfer tool, offering features for redirection and debugging. This extends its utility beyond traditional scanning tasks.
-
Results and GUI Viewer
To improve the user experience, Nmap offers a graphical user interface (GUI) and a results viewer. This allows cybersecurity professionals to analyze and interpret scan results more intuitively.
Nmap's reputation as a comprehensive security and port scanner, coupled with its cross-platform compatibility and additional capabilities as a data transfer tool, positions it as a fundamental tool in the toolkit of cybersecurity experts. Because of its adaptability, it may be used for a variety of network research and security evaluation activities.
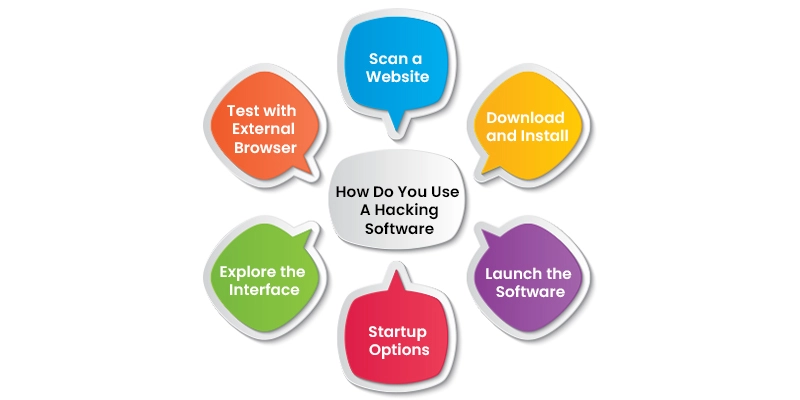
How Do You Use A Hacking Software?
It's important to note that ethical hacking devices and penetration testing should only be conducted on systems and networks where you have explicit authorization. Hacking without authorization is forbidden and can have dire repercussions.
If you're using ethical hacking tools for legitimate security testing purposes, here's a general guide on how to get started:
Download and Install
To download the desired ethical hacking programme, visit the official website or another trustworthy resource. Adhere to the software's installation instructions.
Launch the Software
After installation, launch the hacking tool from your computer.
Startup Options
Configure the startup options based on your testing requirements. This may include specifying the target system, choosing scanning parameters, and setting other preferences.
Explore the Interface
Familiarize yourself with the software's interface. Understand the various features, options, and functionalities available.
Test with External Browser
Many ethical hacking tools allow you to test with an external browser. This helps you simulate real-world scenarios and assess how vulnerabilities may be exploited.
Scan a Website or Perform Penetration Testing
Once you are comfortable with the interface, start scanning a website or perform penetration testing on the target system. Monitor the results and reports generated by the tool to identify vulnerabilities.
Remember to always adhere to ethical hacking guidelines, respect the legal boundaries, and obtain proper authorization before conducting any security testing. If you're unsure about the legality or ethical implications of your actions, seek guidance from relevant authorities or security experts.
Is Using Hacking Tools Legal?
The use of hacking tools is legal under specific conditions, and it is important to distinguish between ethical hacking (white hat hacking) and malicious activities. Here are the key points:
White Hat Hacking
Using hacking tools and techniques for security testing and vulnerability identification in a legal and authorised manner is known as ethical hacking, or "white hat" hacking.
Permission
Getting clear written consent from the target system or network administrator is essential before beginning any kind of security testing. Even when done with good intentions, unauthorised hacking is prohibited.
Authorized Testing
Hacking tools should only be used for authorized penetration testing, security assessments, or vulnerability assessments. This may involve testing websites, networks, or applications to identify and address potential security weaknesses.
Legal and Ethical Boundaries
Hackers who follow ethical and legal guidelines must act morally and legally. Any activities that go beyond the scope of authorized testing or involve unauthorized access to systems can lead to legal consequences.
Professional and Responsible Conduct: Ethical hackers should conduct themselves in a professional and responsible manner. This includes respecting privacy, following ethical guidelines, and reporting identified vulnerabilities to the relevant parties.
It is imperative to stress that utilising hacking tools without the appropriate licence is prohibited and may have serious legal repercussions. When ethical hacking is carried out legally and ethically, it can significantly improve cybersecurity by locating and fixing flaws before bad actors can take use of them. For individuals interested in learning the ethical and legal aspects of hacking, as well as contributing responsibly to cybersecurity practices, considering enrolling in a reputable Ethical Hacking Course in Madurai can provide valuable insights and skills. This learning opportunity provides people with the information they need to navigate the ethical boundaries of hacking devices and contribute effectively to maintaining a secure digital environment.
With the escalating threats to Internet security, organizations are increasingly recognizing the imperative of employing skilled and certified ethical hackers to fortify their defenses against cybercriminal activities. Courses such as the Certified Ethical Hacking (CEH) program are sought after by individuals aiming to develop expertise in ethical hacking. The proactive role of ethical hackers is paramount in identifying and remedying vulnerabilities before malicious entities exploit them, thereby preventing fraudulent crimes and identity thefts. Notably, end users are acknowledged as potential security vulnerabilities, underscoring the importance of user awareness and education in the overall cybersecurity strategy. The surge in high-profile security breaches has accentuated the need for robust cybersecurity measures, with ethical hacking tools playing a pivotal role in assessing and fortifying internet security. These tools assist organizations in identifying weaknesses and potential shortcomings, ultimately averting data breaches. As the digital landscape evolves, In order to handle the ever-changing nature of cyber threats and guarantee a safe and reliable digital environment for both individuals and enterprises, it is essential to upskill in ethical hacking.
