
Vulnerability Assessment and Penetration Testing (VAPT) is a methodology designed to identify security vulnerabilities within software or computer networks. There is a common misconception that VAPT consists of two separate testing processes. However, the optimal approach involves integrating both to achieve more comprehensive results. In Vulnerability Assessment, the primary objective is to identify and rectify bugs, whereas Penetration Testing involves probing and exploiting the system to ascertain the existence of vulnerabilities.
The combination of both processes enhances the overall effectiveness of identifying and addressing security weaknesses. If you're passionate about understanding and addressing these challenges, you might consider enrolling in a Cyber Course in Chennai. Such a course can equip you with the skills and knowledge needed to navigate the intricate landscape of cybersecurity and contribute to the resilience of organizations in the face of cyber threats.
What is a Vulnerability Assessment?
Vulnerability assessment is the process of discovering and quantifying identified security vulnerabilities within an environment. This practice involves a comprehensive evaluation of the information security posture, identifying weaknesses, and proposing mitigation measures to either eliminate or minimize those vulnerabilities to an acceptable risk level.
The General Steps followed in Vulnerability Assessments Include:
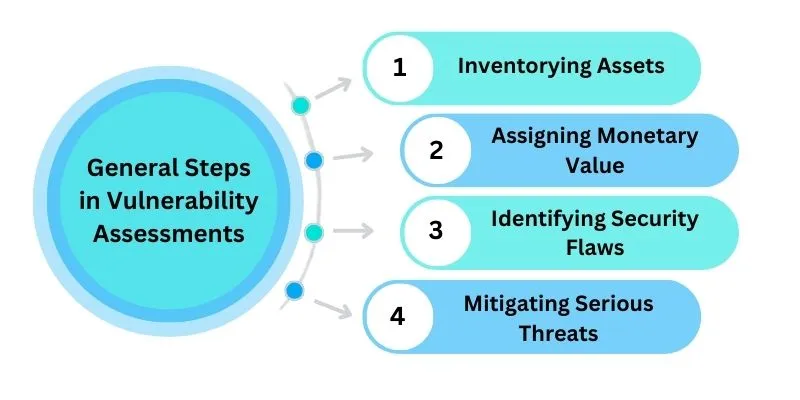
Inventorying Assets and Resources:
Identifying and documenting all assets and resources within the system, providing a comprehensive view of the environment.
Assigning Monetary and Contextual Value:
Determining the monetary and contextual value associated with each resource, considering their importance within the system.
Identifying Security Flaws and Potential Dangers:
Evaluating each resource for potential security flaws and identifying any associated risks or dangers.
Mitigating Serious Threats to Important Resources:
Implementing measures to reduce or eliminate the most critical threats identified, particularly those posed to crucial resources.
By systematically following these steps, vulnerability assessments contribute to a thorough understanding of the security landscape, allowing for informed decision-making and the establishment of effective risk mitigation strategies.
Why Vulnerability Management?
Over the past decade, malicious code, Trojans, complex worms, botnets, DNS attacks, and spam sites have been consistently reported as common cyber-attacks. However, the landscape has evolved, and contemporary cybercriminals are introducing new forms of malware such as bitcoin wallet stealers, ransomware, and POS attacks. These emerging threats pose significant challenges to information security.
The transformation of information security requirements is driven by the rapid evolution of data security standards, as hackers continually devise new methods to infiltrate systems. Businesses face difficulties in adequately preparing for information security incidents in this dynamic environment.
Traditional security measures, including intrusion detection systems, antivirus software, encryption, preventive systems, and patching, remain crucial defenses against known threats. However, the effectiveness of these solutions diminishes over time as intruders develop innovative methods to evade controls.
One notable challenge is the identification gaps in incident detection, which organisations often struggle with due to inherent limitations in their design. These almost unsolvable detection gaps contribute to the difficulty in promptly identifying and addressing data security issues. As a result, organisations need to continually adapt their security strategies to stay ahead of evolving cyber threats.
How can I Know if My Firm Requires a Vulnerability Assessment?
Vulnerability Assessment and Penetration Testing are often underestimated by organisations, yet every company is susceptible to potential cyber threats. This becomes evident in the wake of recent ransomware attacks. It is imperative for organizations to take responsibility and ensure the implementation of adequate security measures to safeguard their applications.
A Vulnerability Assessment is a crucial step that should be conducted at least annually or after implementing significant changes to your application. This proactive approach helps identify and address potential vulnerabilities in the system, fortifying the overall security posture. By regularly assessing and testing the security measures in place, organizations can better protect themselves against evolving cyber threats and mitigate the risk of unauthorised access or data breaches.
The Root Causes of Vulnerabilities
The fundamental causes of system vulnerability often stem from misconfigurations and poor programming practices. Several reasons contribute to vulnerabilities, including:
Defects in Hardware and Software Design
Flaws in the design of both hardware and software components can introduce vulnerabilities to a system. Identifying and addressing these defects is crucial to enhancing overall security.
Inadequately Configured Systems Connected to Unsecured Networks
Systems that are not properly configured, especially when connected to insecure networks, create vulnerabilities. Improper configurations can expose the system to potential threats and compromise its security.
Ineffective Password Combinations
Weak or easily guessable password combinations contribute to system vulnerability. Robust password policies and the use of strong, unique passwords are essential for mitigating this risk.
Complexity of Hardware or Software
Complex hardware or software components can introduce vulnerabilities, as intricate systems may have more potential points of failure. Simplifying configurations and ensuring clear security protocols help address this challenge.
Addressing these vulnerabilities requires a comprehensive approach, encompassing secure design practices, proper configuration management, robust password policies, and a focus on minimizing unnecessary complexity in hardware or software components. Regular assessments, such as vulnerability scanning and penetration testing, can help identify and remediate potential weaknesses in a proactive manner.
What is a Penetration Test?
Penetration testing, often referred to as PEN testing, is a security assessment aimed at identifying vulnerabilities in a network, system, or application that could be exploited by potential attackers. Also known as ethical hacking, individuals conducting these assessments are commonly referred to as 'white hat' hackers. The objective is to emulate the genuine behavior of cyber-criminals, seeking to identify key security weaknesses and vulnerabilities. 'White hat' hackers not only pinpoint these issues but also provide recommendations for remediation.
There are various types of penetration testing services, and the scope can extend beyond the network to include social engineering attacks or physical security assessments. Two common types of penetration tests are "clear box" and "glass box," differing in the level of knowledge the tester possesses about the target systems, with the latter relying on the tester to conduct independent research.
The General Steps Involved in a Penetration Test Include
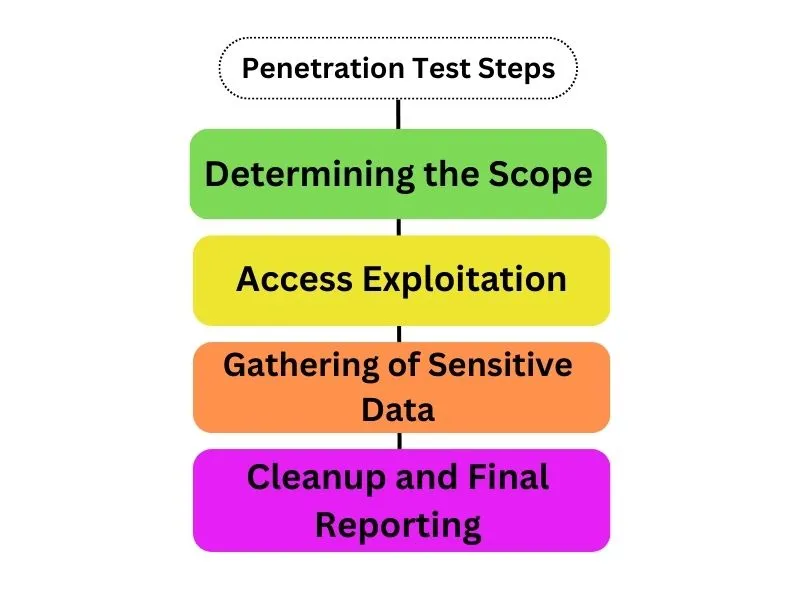
Determining the Scope
Identifying the specific areas or systems within the network, system, or application that will be targeted during the penetration test.
Access Exploitation and Escalation Attempts
Attempting to exploit identified vulnerabilities to gain unauthorized access and escalating privileges within the system.
Testing for the Gathering of Sensitive Data
Assessing the security measures in place to protect sensitive data and testing for potential data breaches.
Cleanup and Final Reporting
Concluding the penetration test by addressing any changes made during the assessment and providing a comprehensive final report. This report typically includes identified vulnerabilities, their severity, and recommendations for remediation.
By following these steps, penetration testing aims to proactively identify and address security vulnerabilities, helping organizations enhance their overall cybersecurity posture. If you're interested in mastering the art of cybersecurity and penetration testing, you may want to explore a Cyber Security Course in Bangalore offered by FITA Academy. Such a course can provide you with the knowledge and practical skills needed to navigate the cybersecurity landscape effectively and contribute to safeguarding digital assets.
Why Penetration Testing?
The objectives of penetration testing encompass various aspects of cybersecurity and risk management.
Here are Some Key Goals
Protect Financial Data in Transit
Ensure the secure transfer of financial data between systems and across networks to prevent unauthorized access or interception.
Safeguard User Information
Implement measures to protect user information, such as personal data and login credentials, from potential breaches or unauthorized access.
Identify Security Weaknesses in Programs
Proactively identify and address security weaknesses within programs or applications to prevent exploitation by potential attackers.
Discover Faults in the System
Uncover and address any faults or vulnerabilities in the system that could be exploited, compromising the overall security posture.
Assess Tolerance for Cyber Hazards
Evaluate the organization's resilience to cyber hazards by simulating real-world scenarios and assessing how well the systems withstand potential threats.
Implement an Efficient Security Plan
Develop and implement an effective security plan within the organization based on the findings from penetration testing. This helps in enhancing overall cybersecurity measures.
Penetration Testing: Discover Hidden Flaws before Hackers do
Penetration testing is a proactive assessment of the entire application or system, aimed at identifying potential vulnerabilities and addressing weaknesses. It serves as an early warning system for security professionals by notifying them when existing security policies are violated. The resolution of security issues is contingent upon uncovering their root causes. Penetration testing surpasses the scope of merely identifying security holes; it simulates the actions of a real-world hacker, infiltrating the system to understand how an intruder might access data. This testing approach not only highlights the effectiveness of security safeguards and rules but also explicitly identifies the gaps through which cyber-criminals could potentially exploit the system. In essence, penetration testing provides a comprehensive evaluation that goes beyond surface-level identification, offering valuable insights into the security posture and aiding in the proactive fortification of the system against potential threats.
Why is VAPT required?
Vulnerability Assessment and Penetration Testing (VAPT) provides several advantages for businesses in terms of security.
Here are Some Key Benefits
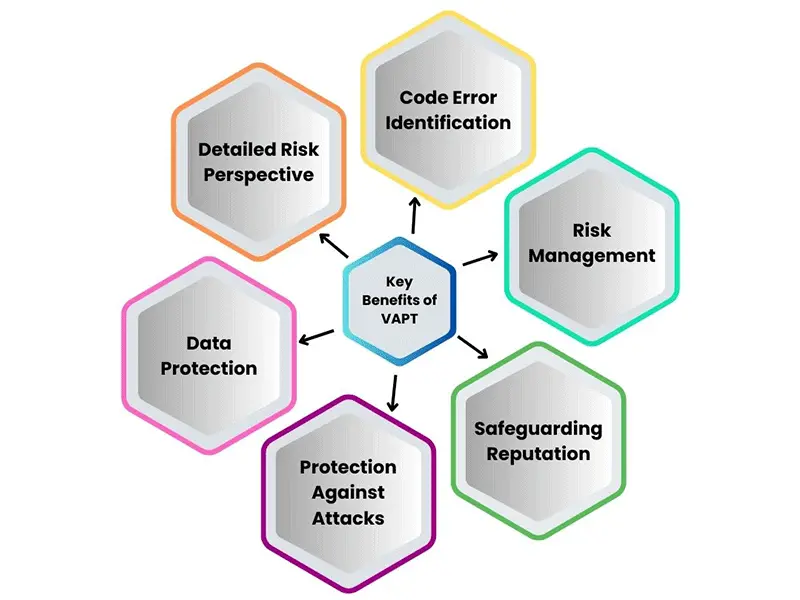
Detailed Risk Perspective
Offers a comprehensive view of potential risks to an organization's applications, helping in the identification of vulnerabilities that could be exploited.
Code Error Identification
Assists the organization in detecting and addressing code errors that may be susceptible to cyber-attacks, enhancing the overall security of applications.
Risk Management
Facilitates effective risk management by identifying and prioritizing vulnerabilities, allowing organizations to focus on addressing high-priority threats.
Safeguarding Reputation and Finances
Protects the company's reputation and financial assets by proactively addressing vulnerabilities, preventing potential breaches that could lead to reputational damage and financial losses.
Protection Against Internal and External Attacks
Enhances the security posture by safeguarding applications from both internal and external attacks, ensuring a holistic defense mechanism.
Data Protection
Acts as a crucial measure in protecting the organization's sensitive data from malicious attacks, maintaining the confidentiality and integrity of critical information.
How Does VAPT Function?
The initial phase of Vulnerability Assessment and Penetration Testing (VAPT) involves identifying the systems and applications that require evaluation. This can be achieved through manual assessment or by utilizing specialized tools. Once the list is compiled, a VAPT tool is employed to systematically scan each system or application for vulnerabilities. These tools employ various techniques, including network mapping, port scanning, and banner grabbing, to identify potential vulnerabilities.
After the completion of the vulnerability assessment, the subsequent step involves conducting a penetration test on the identified vulnerable systems or applications. The primary objective of this test is to exploit vulnerabilities deliberately, aiming to gain unauthorized access to sensitive data or seize control of the system. This two-fold approach, combining Vulnerability Assessment and Penetration Testing, provides a comprehensive evaluation of potential security risks within the targeted systems and applications.
What is a VAPT tool?
A Vulnerability Assessment and Penetration Testing (VAPT) tool combines two essential components: Vulnerability Assessment (VA) and Penetration Testing (PT). The tool performs a Vulnerability Assessment to identify areas of weakness within a system or application. Subsequently, the Penetration Testing component exploits these identified weaknesses to gain unauthorized access. For example, a Vulnerability Assessment may reveal weak encryption, and the Penetration Test will actively attempt to decipher it.
List of VAPT Tools
Intruder
An intruder is an application designed to scan websites for vulnerabilities and identify potential threats to the security of the targeted system.
Metasploit
Metasploit is a robust framework equipped with pre-packaged exploits and code. It leverages a comprehensive database from the Metasploit project, covering a wide range of vulnerabilities and associated exploits.
Nessus
Nessus is a free tool designed to assess the configuration and vulnerabilities of an organization's IT infrastructure on the internet.
Burp Suite Pro
Burp Suite Pro is a powerful toolkit specifically designed for online application security, offering tools for vulnerability analysis and penetration testing.
Aircrack-ng
Aircrack-ng is a set of tools utilized for evaluating the security of wireless networks. Its functionalities include password monitoring, scanning, network attack analysis, and password cracking.
Types of Network VAPT
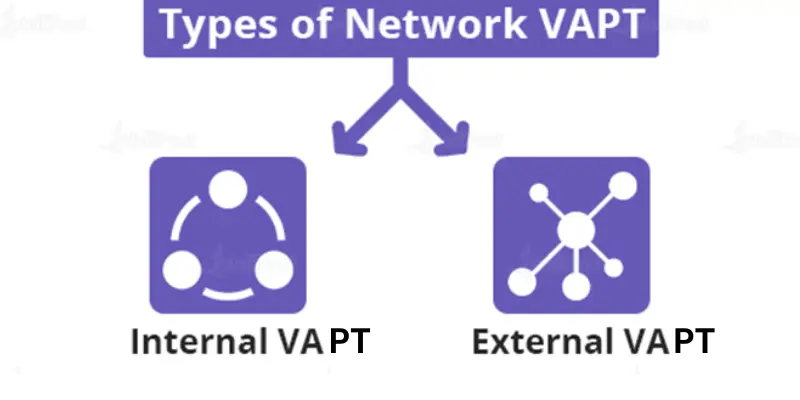
There are two primary types of network vulnerability assessments and penetration testing:
1. Internal VAPT
This type exclusively focuses on the internal network. It involves vulnerability screening for internal servers, firewalls, and data components such as database servers or file servers. Only vulnerability assessment is conducted since the testing is performed from within the network, and penetration testing is not part of the process. Internal security audits can be executed either physically within the network premises or remotely.
2. External VAPT
This type is conducted on the external perimeter of the network, monitoring the internet-facing aspects. Since the testing is done from outside the premises, a comprehensive penetration testing is likely performed after the vulnerability assessment. Vulnerability scanning is employed to detect security flaws or vulnerabilities, while penetration testing endeavors to exploit those identified vulnerabilities.
VAPT Report
A VAPT Testing report serves as a thorough examination of the vulnerabilities identified during the security testing process. It provides detailed insights into the weaknesses, assesses the associated risks, and proposes potential solutions. The Pentest Report encompasses a comprehensive vulnerability analysis, accompanied by Proof of Concept (POC) demonstrations and recommended remediation strategies to address the most critical vulnerabilities. An effective penetration test report also assigns scores to each identified vulnerability, indicating the potential impact on the application or website. This comprehensive documentation is essential for organizations to understand and address security concerns in their digital infrastructure.
Conclusion
The COVID-19 era has significantly altered the landscape of online business operations. Throughout this period, there has been a notable increase in sophisticated and advanced cyber threats targeting businesses globally. In response to these evolving challenges, regular Vulnerability Assessment and Penetration Testing (VAPT) become crucial for ensuring the security and resilience of your organization against potential threats. Regular assessments help identify and address vulnerabilities that could be exploited by cybercriminals, providing a proactive approach to cybersecurity in the dynamic and ever-changing online environment. If you're interested in building expertise in cybersecurity, consider enrolling in a Cyber Security Course in Coimbatore. This course can equip you with the knowledge and skills needed to navigate the complex cybersecurity landscape and contribute to the protection of digital assets.
