In contemporary business landscapes, where about network serve as the central nervous system, the design of these networks significantly influences overall business outcomes. Achieving the ideal equilibrium among network performance, security, redundancy, and cost necessitates a nuanced blend of both project management expertise and technical proficiency. This comprehensive guide aims to empower you in mastering your upcoming network design project. We'll delve into the intricacies of design issues of network layer, furnish a foundational framework to guide your endeavors, and highlight key best practices crucial for success in this critical domain.
Stay tuned to enhance your understanding and execution of strategic network design. If you are passionate about ensuring the security of network designs, consider enrolling in a Cyber Security Course In Bangalore. This course can equip you with the necessary skills and knowledge to navigate the complexities of network security in the dynamic cybersecurity landscape.
What is Network Design?
At its core, network design is a meticulous endeavor involving the planning and conceptualization of a communication network. This intricate process kicks off by delineating both business objectives and technical prerequisites. The journey unfolds methodically, culminating just shy of the network implementation phase – the pivotal stage where planned designs materialize through deployment and configuration efforts.
Network design encompasses a spectrum of critical tasks such as network analysis, IP addressing, hardware curation, and the orchestration of implementation strategies. In uncomplicated scenarios, as witnessed in typical home or small office setups, the network design trajectory is fairly straightforward. However, as the scale expands to encompass extensive enterprise networks, the intricacy of the network design process amplifies significantly, often involving collaboration among diverse stakeholders. Navigating the realm of network design demands a strategic approach, deftly addressing multifaceted considerations for a seamlessly functioning and purposeful communication infrastructure.
Understanding PPDIOO & other network lifecycle models
Before embarking on the intricacies of network design, it's prudent to acquaint ourselves with network lifecycle models. These models elucidate the positioning and role of network design within the overarching lifespan of a network's components and structure.
Among the myriad lifecycle models, Cisco's PPDIOO model (Prepare, Plan, Design, Implement, Operate, and Optimize) stands out as one of the most acclaimed. Embarking on network design involves traversing a comprehensive lifecycle model. Cisco's PPDIOO (Prepare, Plan, Design, Implement, Operate, and Optimize) model serves as an insightful guide through the intricate stages of network development. Let's unravel each phase:
Prepare: Initiating the journey, this phase defines overarching requirements and strategies. Deliverables encompass essential documentation and comprehensive surveys of the current state.
Plan: Delving into specifics, the planning stage tailors network requirements based on the information gleaned in the preparatory phases.
Design: A pivotal stage where information assimilated in the preceding phases is meticulously employed to craft a detailed network design.
Implement: Action unfolds here as the network infrastructure is configured and deployed, often accompanied by rigorous testing to validate the design.
Operate: Transitioning into the production phase, the network undergoes operational use. Monitoring takes center stage, ensuring the network functions as envisioned, with prompt issue resolution.
Optimize: Inevitably, networks require tweaks. This stage identifies changes, and for substantial alterations, the cycle reinitiates with planning and implementation.
Network lifecycle models like Cisco's PPDIOO, Cisco’s PBM (Plan, Build, Manage), and NDLC (Network Development Life Cycle) follow a cyclical pattern. Regardless of the model chosen, the fundamental steps—information gathering, design, implementation, and enhancement—remain constant. The key takeaway lies in comprehending the network lifecycle and discerning the pivotal role of network design within it.
Designing a Network Step-by-Step
Embarking on the journey of network design requires a systematic approach. Here’s a detailed walkthrough of the process, adaptable to the unique needs and complexities of your network infrastructure:
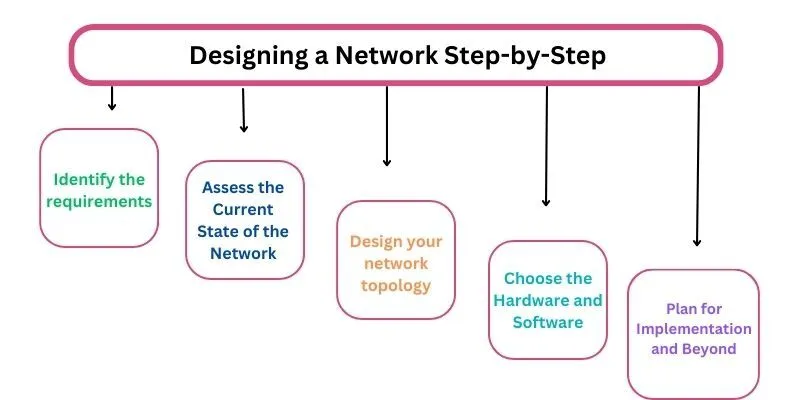
1. Identify the requirements
The commencement of any network design endeavor demands a meticulous process of information gathering and requirement delineation. Establishing unequivocal business and technical prerequisites is paramount, serving as the bedrock for the entire design framework.
Business Requirements
The nexus of your network design initiative lies in understanding and addressing business imperatives. This entails objectives such as:
- Supporting New Offices: Facilitating the expansion of infrastructure to accommodate new offices.
- Enhancing End-User Experience: Focusing on optimizing the experience of end-users interacting with the network.
- Cost Reduction: Strategizing to cut down operational costs effectively.
- Regulatory Compliance: Aligning with new regulations to ensure adherence.
- Business Continuity Improvement: Enhancing strategies for maintaining seamless operations, especially during disruptions.
In accordance with the PPDIOO model's "Prepare" stage, collaboration with stakeholders is pivotal in crystallizing business requirements.
Technical/Functional Requirements
Transitioning to the technical realm, specific functional requirements need meticulous consideration. This encompasses elements like:
- Bandwidth: Determining the network's data transfer capacity requirements.
- Security Measures: Outlining robust security protocols and measures.
- Protocol Specifications: Identifying and incorporating specific protocols integral to the project.
- RTO/RPO Metrics: Establishing Recovery Time Objective and Recovery Point Objective metrics for contingency planning.
- Uptime SLAs: Defining Service Level Agreements pertaining to network uptime.
Moreover, constraints, both financial and technological, must be factored in during requirement formulation. Budgetary constraints for business requirements and legacy app support constraints for technical requirements exemplify the importance of a holistic approach in this foundational phase.
2. Assess the Current State of the Network
Embarking on a network design endeavour often involves confronting an existing infrastructure, and comprehending its current state is a crucial preliminary step. This circumstance can present both facilitative and challenging aspects to the project.
Assessing the Existing Network
Understanding the prevailing conditions of the network is instrumental in making informed design decisions. Several key facets necessitate scrutiny:
- Structured Cabling: The presence of pre-existing structured cabling, such as Cat5 or Cat6A, can either streamline the process or pose challenges based on compatibility with the project's requirements.
- Network Layout: An in-depth comprehension of the current network layout is essential, encompassing the arrangement of devices, servers, and network components.
- Performance Metrics: Evaluating the network's performance parameters provides insights into its capabilities and limitations.
- Data Flows: Analyzing the patterns of data flow within the network aids in optimizing connectivity and efficiency.
- Applications & Services: Identifying the spectrum of applications and services operating on the network is pivotal for tailoring the design to specific functionalities.
- Network Security: Scrutinizing existing security measures and vulnerabilities establishes a foundation for reinforcing or restructuring security protocols.
- Physical and Logical Layout: Delineating the physical and logical organisation of the network offers a comprehensive understanding of its structural dynamics.
Tools and Techniques
This comprehensive assessment relies on a blend of approaches:
- Reviewing Existing Documentation: Examining network diagrams, policies, and monitoring tools provides a foundational understanding.
- Automatic Network Mapping Tools: Leveraging automated tools for network mapping facilitates an accurate depiction of the current state.
- Security Scanners: Employing security scanners aids in uncovering vulnerabilities and fortifying the network against potential threats.
At the culmination of this phase, a nuanced comprehension of the existing network lays the groundwork for subsequent design decisions.
3. Design your network topology
Embarking on the design phase involves delineating the functional components of the network, encompassing both physical and logical considerations. This intricate process involves addressing a spectrum of aspects to create a robust blueprint aligning with specified requirements.
Physical Network Design
The physical aspects of the network design require meticulous planning to ensure optimal functionality and efficiency:
- Cabling Infrastructure: Decisions regarding the deployment of copper and fiber cabling are pivotal, impacting network performance and scalability.
- Switch Port Allocation: Determining the number of switch ports needed is essential for accommodating connected devices seamlessly.
- WiFi Access Point Placement: Strategically positioning WiFi access points optimizes coverage and connectivity within the network.
- Rack Configuration: Planning the layout of racks involves optimizing space, ensuring efficient cooling, and facilitating accessibility for maintenance.
- Cooling and Power: Adequate provisions for cooling systems and power supply must be factored in to maintain an optimal operating environment.
Logical Network Design
Addressing the logical components of the network involves conceptualizing the digital framework and operational architecture:
- IP Addressing and Subnetting: Efficient allocation of IP addresses and subnetting is crucial for streamlining communication and resource management.
- VLAN Implementation: Implementing Virtual Local Area Networks (VLANs) enhances network segmentation, security, and resource allocation.
- Data Flows: Charting the pathways of data flow within the network ensures optimized connectivity and data transfer.
- Network Topology: Defining the network and finding which topology is best in establishing the interconnection patterns between devices, influencing performance and scalability.
- Creating a Static Map: By the conclusion of this phase, a comprehensive static map detailing the physical and logical facets of the network design should materialise. This map serves as a foundational reference for subsequent implementation and optimisation.
- Core Layer: Serving as the network backbone, the core layer facilitates traffic routing between disparate geographical sites. High-throughput core routers are deployed in this layer, emphasising efficiency and reliability.
- Distribution Layer: Situated between the core and access layers, the distribution layer acts as a boundary, implementing network policies. It regulates data flows between various subnets within the network. Cost-effective routers and Layer 3 switches are pivotal components of the distribution layer.
- Access Layer: Dedicated to endpoint devices like user PCs, printers, and VoIP phones, the access layer functions as the interface for these devices. Access switches, handling packet switching and traffic routing play a vital role in this layer.
- Top-Down Design: In the top-down paradigm, the design process commences at the application layer of the OSI model and progressively descends through each layer, culminating at the physical layer. This method aligns with the comprehensive understanding of business requirements, allowing the translation of overarching goals into a detailed network design. While recognized for its strategic alignment with business objectives, the top-down approach is often deemed time-intensive.
- Bottom-Up Design: Conversely, the bottom-up design unfolds by initiating at the physical layer and ascending through the OSI model layers. This approach tends to expedite the design process, providing a quicker overview of the network's physical attributes. However, its drawback lies in the potential oversight of critical requirements or compromises as the design trajectory is predefined before reaching the application layer where user-centric functionalities come into play.
- Milestones: Define key project milestones to ensure a structured and organized deployment process.
- Change Management: Incorporate change management protocols to seamlessly adapt to evolving project dynamics.
- Deliverables: Clearly outline essential deliverables to maintain project focus and accountability.
- Transparency: Maintain transparent and open communication with stakeholders to keep them informed about project progress.
- Expectations: Manage expectations by conveying the anticipated timelines and outcomes of the implementation.
- Validation: Design a robust testing framework, including small-scale deployments for validation before full-scale implementation.
- Verification: Ensure rigorous testing to verify the functionality and performance of the network design.
- Team Handover: If different teams handle implementation and management, devise a seamless transition plan for effective handover.
- Responsibility Clarity: Clearly articulate responsibilities for ongoing management and maintenance.
- Monitoring: Develop a plan for continuous monitoring to promptly identify and address potential issues.
- Maintenance: Establish protocols for routine maintenance, ensuring the sustained optimal performance of the deployed network.
- Hostnames (e.g., printer5.office2.lan3)
- Hardware models
- IP address schemes
- Cable colours (e.g., assigning one colour for VoIP and another for data)
- Security policies
By the conclusion of this phase, a comprehensive static map detailing the physical and logical facets of the network design should materialise. This map serves as a foundational reference for subsequent implementation and optimisation.
Hierarchical Network Layers
A foundational principle in network design is the hierarchical organisation into three distinct layers, each managing specific facets of dataflows:
While the traditional model encompasses all three layers, some networks may forgo the distribution layer, adapting the hierarchical structure to their specific requirements.
Top-Down vs Bottom-Up Design
The strategies of top-down and bottom-up design stand as pivotal methodologies in network design, both grounded in the Open Systems Interconnection (OSI) model. These approaches offer distinctive trajectories in constructing network architecture, navigating through layers from application to the physical layer in the top-down approach, and inversely in the bottom-up model.
These design approaches offer distinct perspectives, and the choice between them hinges on factors such as project scope, complexity, and the emphasis on overarching vision versus detailed components. The selected approach profoundly influences the design process, shaping the network's ultimate structure and functionality.
4. Choose the Hardware and Software
The strategic step of hardware and software selection in network design involves meticulous decision-making to bring the envisioned network infrastructure to life. This crucial phase, often concurrent with earlier steps, demands a judicious choice of specific components like cables, racks, network devices, servers, applications, and cloud services.
Parallel Development
In certain scenarios, the hardware and software selection aligns with the preceding phases of network design. Parallel development may occur, with certain elements being specified early in the project. However, the general principle favors postponing the selection until the network's functional requirements are clearly delineated. This sequential approach ensures optimal flexibility and adaptability to the identified needs.
Flexibility through Delayed Decision-Making
Delaying the selection until the network's purpose is clearly defined allows for greater flexibility. This approach ensures that the chosen hardware and software align precisely with the articulated functional necessities. Additionally, it mitigates the risk of investing in components that may later prove incompatible or insufficient for the network's intended tasks.
Considerations for Custom Parts and Supply Chain
The selection process encompasses a diverse array of components, from standard network devices to custom parts. Particularly for the latter or large-scale orders, awareness of potential supply-chain challenges becomes imperative. Delays in acquiring structured cabling or access switches, for instance, can impede project completion timelines. Proactive considerations for supply-chain dynamics contribute to seamless execution.
In essence, the strategic selection of hardware and software emerges as a pivotal phase, converging the conceptual design into a tangible network reality. The judicious choice of components, guided by functional requirements and a keen awareness of supply-chain nuances, plays an important role in implementing the planned network architecture.
5. Plan for Implementation and Beyond
With the comprehensive network design and hardware/software selections in place, the crucial transition to implementation planning marks the juncture where conceptualization evolves into tangible deployment. This strategic step involves formulating a meticulous plan to execute the deployment, configuration, and testing of the network. For more extensive networks, a phased approach may encompass small-scale test deployments to validate the design's efficacy before full-scale implementation.
Key Components of Implementation Planning
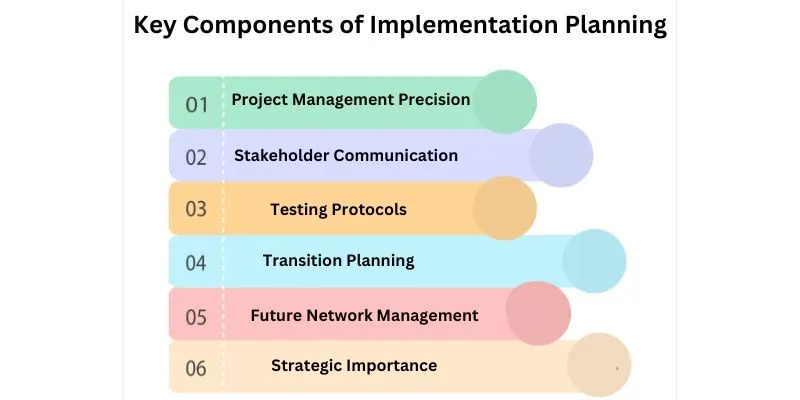
Project Management Precision
Stakeholder Communication
Testing Protocols
Transition Planning
Future Network Management
Strategic Importance
Implementation planning serves as the bridge between the conceptual vision and the operational reality of the network. Precise project management, transparent stakeholder communication, rigorous testing, seamless transitions, and proactive planning for ongoing management collectively contribute to the success of the implementation phase. By addressing these key components, organizations can navigate the intricate landscape of network deployment with efficiency and strategic foresight.
Top 5 Network Design Best Practices
With a framework in place, let's examine some best practices for network architecture to help us make smarter choices along the way.
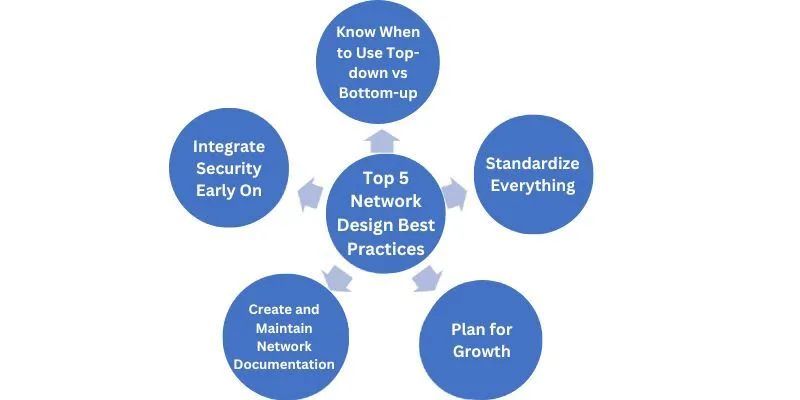
1. Integrate Security Early On
In the domain of network design, a fundamental and highly effective best practice involves the early integration of security measures right from the project's initiation. The principle of "shifting security left," widely embraced in DevOps, underscores the importance of introducing security considerations at the forefront of the development lifecycle. This strategic approach offers multifaceted advantages, preventing security gaps and optimising overall network performance by circumventing the retrospective addition of security measures, a process prone to inefficiencies and oversights.
2. Know When to Use Top-down vs Bottom-up
In instances where a project is initiated without an existing framework, opting for a top-down design approach is generally considered the more favourable choice. This method involves concentrating on the business requirements, thus enhancing the likelihood of achieving accurate results.
Nevertheless, certain network design projects may not warrant the resource and time commitment associated with a top-down approach. For instance, when one is already well-acquainted with an organisation's overarching business requirements, and the task primarily involves expanding a network planning or boosting bandwidth, adopting a bottom-up strategy can prove to be significantly more efficient.
3. Standardize Everything
When standardisation is feasible, it is advisable to implement it. This practice facilitates streamlined troubleshooting, patching, maintenance, and asset management over the long term.
Consider Standardising the following Elements for Enhanced Efficiency:
By adhering to standardised practices in these areas, you not only simplify operational processes but also contribute to a more cohesive and manageable infrastructure. If you are interested in delving deeper into cybersecurity practices and enhancing your skills, you might consider enrolling in a Cyber Security Course in Chennai. This course can provide you with valuable insights and hands-on experience to navigate the intricacies of cybersecurity and contribute effectively to the security of digital systems.
4. Plan for Growth
Anticipating changes in network bandwidth consumption is crucial, recognising that it is bound to evolve over time. It is imperative to contemplate the anticipated increase in bandwidth consumption throughout the network's lifecycle and incorporate this foresight into the design.
While the straightforward solution is to augment bandwidth in alignment with expectations, it is equally vital to ensure that the network is inherently flexible and modular. This flexibility is paramount for effortless accommodation of future expansions. Given the uncertainty surrounding specific future requirements, designing with the awareness that network extension may become necessary remains a prudent strategy. By prioritising a design that allows for seamless scalability, you position the network to adapt dynamically to evolving demands.
5. Create and Maintain Network Documentation
The absence, outdated status, or incompleteness of network documentation represents a significant contributor to technical debt, time wastage, and heightened frustration. To mitigate these issues, it is highly advisable to prioritise comprehensive documentation in your network design and implementation deliverables, specifically covering layers 1 to 3. This documentation should encompass network maps that offer insights into the physical and logical aspects of the design issues of network layer.
Ensuring the creation of these maps is merely the initial step; the ongoing maintenance of such documentation is equally crucial. Regular updates and reviews will not only assist your future self but also prove invaluable to network planning. By committing to this practice, you enhance the efficiency of troubleshooting, reduce downtime, and contribute to an overall smoother network management experience.
Considerations for Designing Computer Networks
Designing a network involves a multitude of considerations, and while factors such as copper vs fibre, logical topologies, IP addressing, VLANs, bandwidth, and WiFi coverage are apparent. Check out FITA Academy for info.
The Following Additional Key Aspects should not be Overlooked:
Regulatory Requirements
Ensure compliance with legal regulations affecting both physical and logical aspects of the network design. Local building codes, National Electrical Code (NEC) requirements, and data protection regulations like HIPAA, PCI DSS, and GDPR should be factored into the design for a fully compliant network planning.
Network Resilience and Redundancy
Recognise the critical need for network availability in business operations and incorporate fault tolerance measures. Modern network designs often include N+1, 2N, or 2N+1 redundancy. However, the level of resilience should be balanced against the associated costs, considering factors such as downtime expenses and the desired level of uptime (e.g., five-nines or 99.999%).
Cloud vs. On-Premises
Assess whether an on-premises or cloud network is more suitable based on business and technical requirements. Given the evolving landscape, it's essential to avoid rigid commitments to on-premises solutions without considering the potential benefits of cloud alternatives or vice versa.
Cooling and Power
Do not underestimate the importance of addressing cooling and power requirements. Failure to meet power needs can impede deployment, and inadequate cooling can lead to equipment overheating and premature failure. Considerations include ensuring electrical infrastructure compatibility, accounting for Power over Ethernet (PoE) loads in UPS sizing, and evaluating server room cooling capacity.
Remember that there is no one-size-fits-all network design. Tailor your approach to align with specific business requirements, and recognise that network design is an ongoing process, extending beyond the initial planning stage as illustrated by network lifecycle models like PPDIOO. For comprehensive insights into designing secure and efficient networks, consider enrolling in a Cyber Security Course in Coimbatore, where you can acquire valuable skills and knowledge to fortify network infrastructures against evolving threats.
