
In today's computerized world, web apps have become essential to our personal and professional life. However, as their prevalence grows, so does the threat of malicious attacks. SQL Injection is one such attack that poses a serious danger to the security and integrity of your web applications and databases. In this blog, we will go into the world of sql injection attacks, investigating their mechanics, potential effects, and effective preventative approaches for protecting your applications from this persistent threat.
Enroll in SQL Online Training and gain in-depth knowledge of SQL injection techniques and understand the methods to prevent and mitigate vulnerabilities. FITA Academy offers comprehensive training in this field, providing you with valuable knowledge and skills.
SQL Injection
SQL Injection is a malicious attack technique that exploits flaws in the database layer of a web site. It entails introducing malicious SQL statements into the input fields of an application, which are then executed by the database. SQL Injection's primary purpose is to alter or extract private data from the database, modify its contents, or even obtain unauthorized access to the underlying system.
How to perform SQL Injection?
Before launching a SQL Injection attack, the attacker must first find vulnerable user inputs on the website or application. A web page or application inserts user input directly into a SQL query in the case of a SQL Injection vulnerability. The attacker can create a malicious payload, which is the attack's critical element. When the attacker delivers this payload, the database executes the malicious SQL commands included in it.
Here is a sql injection example explaining how it performs: Let's consider a simple web application that has a login form consisting of two fields: username and password. The application uses these inputs to construct an SQL query to authenticate the user. Here's a simplified version of the code that handles the login functionality:
$username = $_POST['username'];$password = $_POST['password'];$query = "SELECT * FROM users WHERE username = '$username' AND password = '$password'";Before generating the query, the application would validate the user inputs in a secure setting. However, such steps have yet to be applied in this sensitive case.
An attacker with malicious intent could exploit this flaw by tampering with the input fields. For example, rather than entering a proper username and password, the attacker might put the following value in the username field:
' OR '1'='1This input modifies the query's logic when inserted into the SQL query. The resulting query would be:
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = '$password'Since '1'='1' is always true, the attacker effectively bypasses the password check. This means the attacker can log in without a valid password, gaining unauthorized access to the application.
Furthermore, an attacker can exploit SQL Injection to extract sensitive information from the database. For instance, if the application displays user information on a profile page, the attacker can manipulate the username field to extract data from other users. Here's an example:
' UNION SELECT username, password FROM users WHERE '1'='1Modified Query
SELECT * FROM users WHERE username = '' UNION SELECT username, password FROM users WHERE '1'='1' AND password = '$password'Now, the attacker would receive their information and the usernames and passwords of all users stored in the database.
These examples demonstrate how sql injection attack can exploit vulnerabilities in poorly constructed SQL queries, allowing attackers to manipulate queries, bypass authentication, and extract sensitive information.
It is very important to implement proper input validation, parameterized queries, and other preventive measures to mitigate the risk of SQL Injection attacks and protect your web applications and databases.
What causes SQL Injection Attacks?
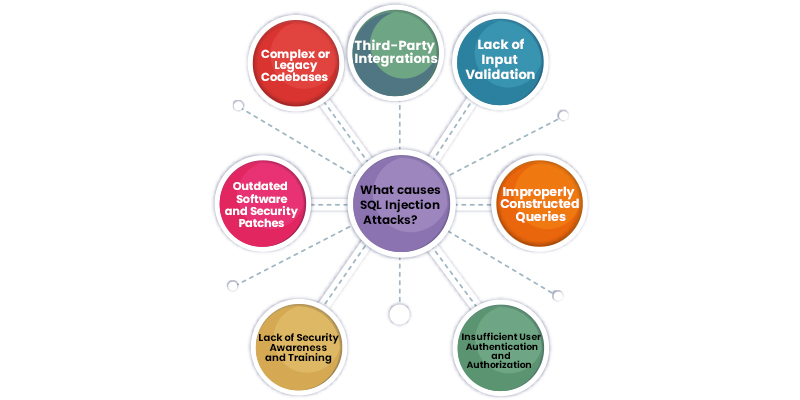
SQL Injection attack is caused due to vulnerabilities in web applications that allow attackers to manipulate SQL queries. Listed below are some factors that contribute to the occurrence of SQL Injection attacks:
- Lack of Input Validation: Not validating and sanitizing user inputs significantly causes SQL Injection attacks. When user inputs are not properly validated, attackers can inject malicious SQL code into input fields, which is then executed by the application's database.
- Improperly Constructed Queries: Vulnerabilities can arise due to insecure coding practices, such as directly incorporating user inputs into SQL queries using concatenation. If user inputs are directly inserted into queries without proper sanitization, attackers can manipulate the queries structure and execute unintended commands.
- Insufficient User Authentication and Authorization: Weak authentication and authorization mechanisms can provide opportunities for SQL Injection attacks. Insufficient validation of user credentials and inadequate enforcement of access controls within an application can expose vulnerabilities that attackers can exploit to achieve unauthorized access to sensitive data or engage in unauthorized activities.
- Lack of Security Awareness and Training: Insufficient knowledge and awareness among developers and system administrators about secure coding practices and potential attack vectors can contribute to SQL Injection vulnerabilities. Developers may introduce vulnerabilities into the application without proper training and understanding of the risks.
- Outdated Software and Security Patches: Failure to keep web applications, frameworks, and database management systems updated with the latest security patches can leave them vulnerable to known exploits. Attackers often target outdated software versions that have known vulnerabilities that can be exploited, including those related to SQL Injection.
- Complex or Legacy Codebases: Large and complex codebases, particularly those developed over a long period, can be challenging to secure. Older or legacy systems may have yet to incorporate modern security practices, making them more susceptible to sql injection attack.
- Third-Party Integrations: Integrating third-party libraries, modules, or components into an application introduces potential vulnerabilities. If these components have SQL Injection vulnerabilities, they can be exploited to compromise the entire application.
Enrolling in MySQL Online Training can benefit you to acquire comprehensive knowledge of safeguarding databases from SQL injection vulnerabilities and understanding the methods to prevent potential attacks.
Understanding these causes of SQL Injection attacks is crucial for developers, system administrators, and security professionals. By addressing these vulnerabilities through proper input validation, secure coding practices, regular patching, and security training, organizations can significantly reduce the risk of SQL Injection attacks and enhance the overall security of their applications.
Types of SQL Injection Attacks
- Error-Based SQL Injection attack:
Attackers use a sophisticated technique to extract information from a database by exploiting error messages generated by the database server. It takes advantage of SQL statements that generate error messages containing valuable information about the database structure or the data it holds.
- A Union-Based SQL Injection Attack:
It is a type of SQL Injection attack where an attacker exploits vulnerabilities in a web application's input validation and query construction to manipulate the application's SQL queries and retrieve unauthorized information from the database. The attacker injects a crafted SQL payload into the input fields of the application, typically in parameters used in SQL queries. The payload typically includes a UNION SELECT statement that retrieves data from a different table or additional columns in the same table. A Union-Based SQL Injection attack aims to obtain sensitive information from the database, such as usernames, passwords, or other confidential data.By leveraging the UNION statement and carefully constructing the injected payload, the attacker can retrieve and extract data they would otherwise not have access to.
- Blind SQL Injection attack:
It is a type of SQL Injection attack where an attacker exploits vulnerabilities in a web application's input validation and query execution to extract information from the database, even without direct feedback or visible error messages from the application. It is further classified into Boolean based and Time based SQL Injection attacks.
SQL Injection payloads
Sql injection payloads refer to the malicious code or input that attackers inject into vulnerable web applications to exploit SQL Injection vulnerabilities. These payloads are specifically crafted to manipulate the behavior of SQL queries executed by the application's database. SQL Injection payloads are designed to exploit the lack of input validation and improper handling of user-supplied data in an application.
By injecting these payloads, attackers can alter the intended structure and execution of SQL queries, potentially gaining unauthorized access, extracting sensitive data, modifying or deleting database records, or executing arbitrary commands on the underlying system.
SQL injection in Cybersecurity
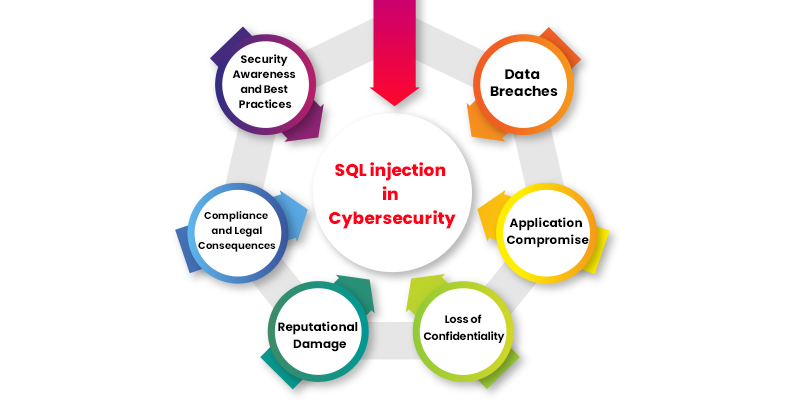
SQL Injection plays a significant role in Cybersecurity as it severely threatens the confidentiality, integrity, and availability of data within web applications and databases. Understanding and addressing SQL Injection vulnerabilities is crucial in maintaining a robust security posture. Here are the key roles of sql injection in cyber security:
- Data Breaches
- Application Compromise
- Loss of Confidentiality
- Reputational Damage
- Compliance and Legal Consequences
- Security Awareness and Best Practices
You can join Cyber Security Course in Chennai to pursue your aspirations of learning about SQL dominance in cybersecurity and its practical applications.
What are the Prevention Techniques for SQL Injection Attacks?
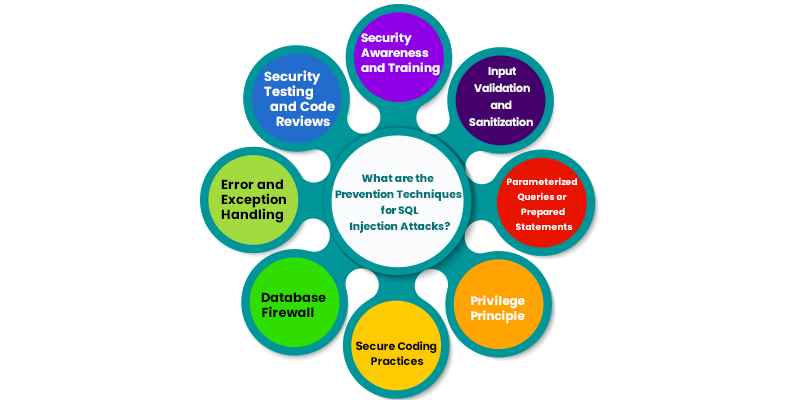
Many SQL Injection prevention techniques and measures are implemented to safeguard web applications and databases from SQL Injection attacks. These techniques aim to reduce the risks associated with improperly handled user input and exploiting vulnerabilities within SQL queries. Regular security assessments and continuous monitoring should also be part of an overall cybersecurity strategy to ensure ongoing protection against evolving threats. Here are the definitions of commonly employed sql injection prevention techniques:
- Input Validation and Sanitization: Input validation involves examining user-supplied data to ensure it meets expected criteria, such as data type, length, and format. On the other hand, sanitization involves removing or encoding special characters from user input to prevent malicious SQL statements.
- Parameterized Queries or Prepared Statements: Parameterized queries or prepared statements separate SQL code from user input by treating input values as parameters.
- Privilege Principle: The principle of least privilege dictates granting users and database accounts only the minimum privileges necessary to perform their intended tasks.
- Secure Coding Practices:Secure coding practices follow established guidelines and frameworks prioritizing security.
- Database Firewall: A database firewall is a security measure that monitors incoming and outgoing traffic to and from a database.
- Error and Exception Handling: Proper error and exception handling are essential to avoid leaking sensitive information that could aid attackers.
- Security Testing and Code Reviews: Security testing, including vulnerability assessments and penetration testing, helps identify and address SQL Injection vulnerabilities. Regular code reviews by knowledgeable professionals ensure that secure coding practices are followed consistently, and vulnerabilities are addressed promptly.
- Security Awareness and Training: Educating developers, administrators, and other stakeholders about the risks and prevention techniques associated with SQL Injection is important. Training programs on secure coding practices and the importance of input validation and sanitization help create a security-conscious culture and enhance overall defense against SQL Injection.
Master Cyber Security techniques and understand the various types of Cyber attacks by enrolling in Cyber Security Course in Bangalore where you can gain knowledge of Cybersecurity practices, learn how to defend against different types of attacks, and develop skills to protect digital systems and data effectively.
In conclusion, sql injection attack is a significant threat to the security of web applications and databases, potentially leading to unauthorized access, data breaches, and reputational damage. However, by understanding the nature of SQL Injection and implementing effective prevention techniques, organizations can mitigate these risks and enhance their cybersecurity posture.
